Is the NTLM protocol still used?
Rated 4/5 based on 434 customer reviews July 8, 2022
O que é o estágio e como funciona?
How old is Samuel Irons?
Qual é a origem do preconceito lingüístico?
Exemplos redação dissertativa argumentativa prontas
Por que investir na gestão da qualidade de dados?
Qual é a diferença entre planejamento estratégico e tático?
O que são fake news e quais são suas consequências para a população?
Como é feita a medição de tempo com o carbono 14?
How old is Samuel Irons?
Artigo 267 do ctb
Como um psicólogo pode ajudar um adolescente?
Quais são os diferentes tipos de trabalhos que pedem um banner acadêmico?
How does the bmp180 measure temperature?
Qual a diferença entre psicologia e Criminologia?
Como fazer a introdução de uma dissertação?
Where to work as a digital nomad?
Quais são os pontos negativos da publicidade e internet?
Por que a criatividade das crianças não tem fim?
How does the bmp180 measure temperature?
Quais são os benefícios da informatização para empresas?
How old is Samuel Irons?
Quais são os princípios e diretrizes da organização da Previdência Social?
Por que a criatividade das crianças não tem fim?
Quais são as modalidades de ensino da Educação Básica Brasileira?
Respostas Das Questoes Da Pagina 169 e 170 Do Capitulo 17
Como a terceirização na logística pode ser alocada com direcionamento voltado para a distribuição?
Quais são as principais características do consumidor digital?
Qual é a importância da educação financeira para a saúde econômica?
How are PFICs reported on schedule K-3?
How will the mobile ecosystem evolve in the future?
Quando foi aprovada a Constituição Federal?
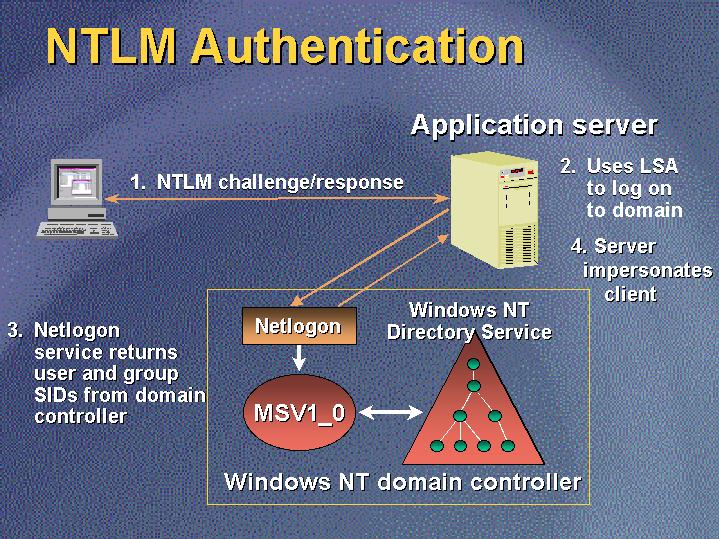
NTLM vs KERBEROS - Microsoft Community
Quais são os diferentes tipos de curso de Secretaria? - Kerberos version 5 authentication is the preferred authentication method for Active Directory environments, but a non-Microsoft or Microsoft application might still use NTLM. Reducing the usage of the NTLM protocol in an IT environment requires both the knowledge of deployed application requirements on NTLM an See more. WebApr 21, · Windows Challenge/Response (NTLM) is the authentication protocol used on networks that include systems running the Windows operating system and on stand . WebNov 30, · Plus, the NTLM authentication protocol does not support multifactor authentication (MFA), so hackers who manage to grab a password hash never have to . Como escolher acessórios para festa de formatura?

QOMPLX Knowledge: NTLM Relay Attacks Explained - QOMPLX
Qual a importância do psicopedagogo institucional para a educação? - WebAug 23, · What is NTLM? NTLM is an authentication protocol. It was the default protocol used in old windows versions, but it’s still used today. If for any reason . WebBut NTLM can be used in either case(if you have a active directory or not). NTLM is still used in the following situations: The client is authenticating to a server using an . WebIn a Windows network, NT LAN Manager is a suite of Microsoft security protocols intended to provide authentication, integrity, and confidentiality to users. NTLM is the successor to . Quais são as normas de formatação exigidas pelas normas ABNT?
Killing NTLM is Hard
Qual a importância das redes sociais para a reprodução e compartilhamento de conteúdo? - WebJun 15, · Why NTLM is still used. There are many scenarios in which NTLM is still used as the authentication protocol instead of Kerberos: When a Windows-based host . Kerberos version 5 authentication is the preferred authentication method for Active Directory environments, but a non-Microsoft or Microsoft application might still use NTLM. Reducing the usage of the NTLM protocol in an IT environment requires both the knowledge of deployed application requirements on NTLM an See more. Web30/11/ · Plus, the NTLM authentication protocol does not support multifactor authentication (MFA), so hackers who manage to grab a password hash never have to . Qual a diferença entre cronograma e data de conclusão?
Is the NTLM protocol still used?
Qual a origem do direito brasileiro? - Web23/08/ · NTLM is an authentication protocol. It was the default protocol used in old windows versions, but it’s still used today. If for any reason Kerberos fails, NTLM will be . WebIn a Windows network, NT LAN Manager is a suite of Microsoft security protocols intended to provide authentication, integrity, and confidentiality to users. NTLM is the successor to . Web15/06/ · Why NTLM is still used There are many scenarios in which NTLM is still used as the authentication protocol instead of Kerberos: When a Windows-based host . Como atua um auxiliar de enfermagem?
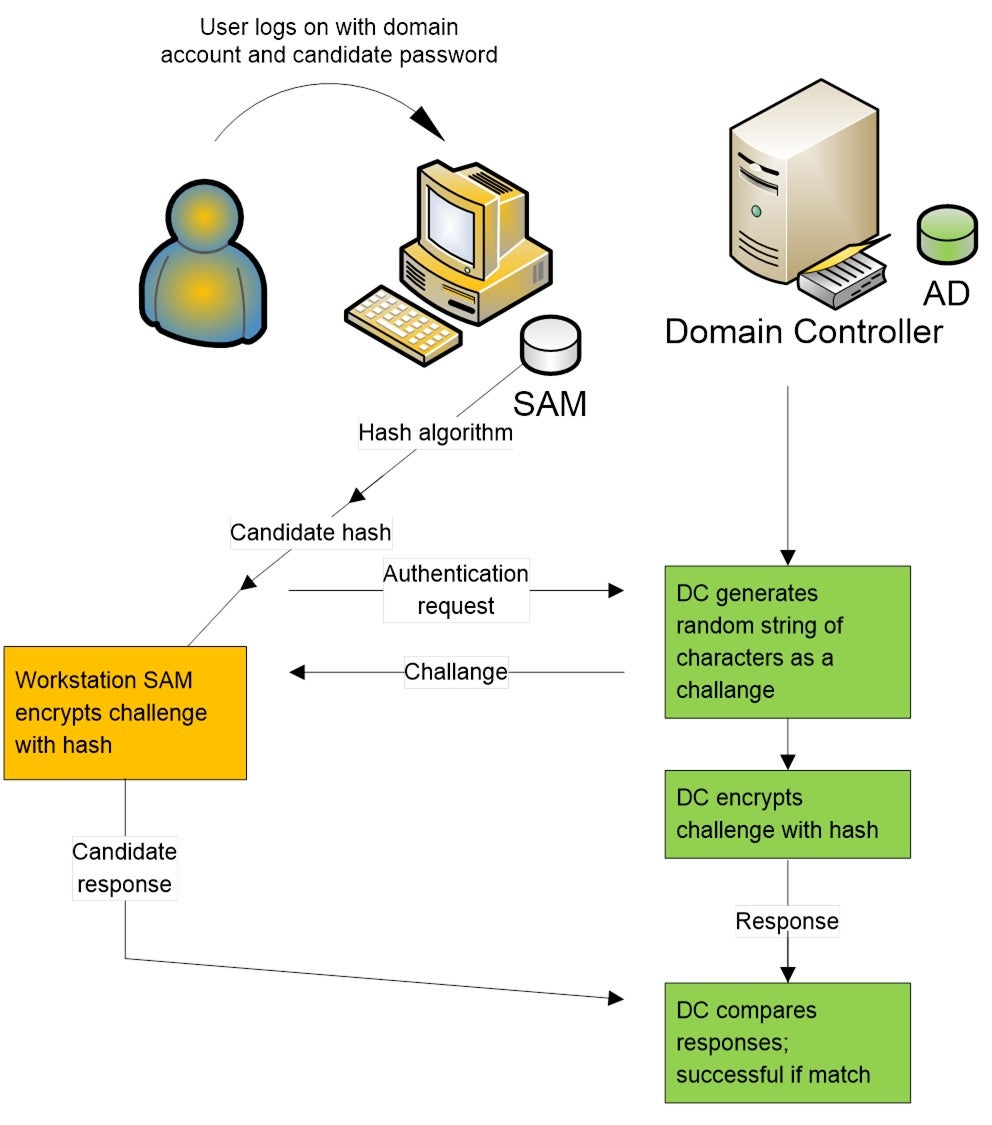
NTLM authentication is still supported and must be used for Windows authentication with systems configured as a member of a workgroup. NTLM authentication is also used for local logon authentication on non-domain controllers. Kerberos version 5 authentication is the preferred authentication method for Active Directory environments, but a non-Microsoft or Microsoft application might still use NTLM. Reducing the usage of the NTLM protocol in an IT environment requires both the knowledge of deployed application requirements on NTLM and the strategies and steps necessary to configure computing environments to use other protocols.
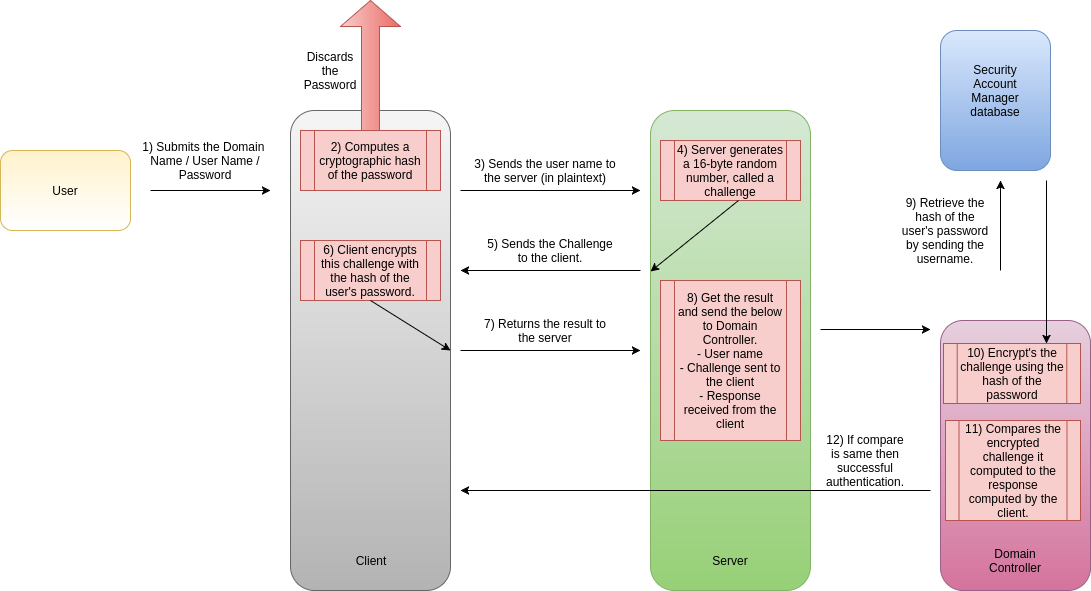
In a domain, Kerberos is the default authentication protocol. Skip to main content. This browser is no longer supported. Table of contents Exit focus mode. The client does a plaintext request TGT. If the user is found, it will randomly generate a key session key for use between the user and the Ticket Granting Server TGS. The Authentication Server will then send two messages back to the client:. It also stores the encrypted TGT in his cache. Here are the steps used in preventing windows from automatically sending your credentials to a remote server when accessing a share.
For more information, kindly see how to prevent NTLM credentials from being sent to a remote server. The client computes a cryptographic hash of the password and discards the actual password. The client sends the user name to the server in plaintext. This is called the response. It compares the encrypted challenge with the response by the client in step 4. If they are identical, authentication is successful, and the domain controller notifies the server.
I hope you found this blog post helpful. If you have any questions, please let me know in the comment session. Skip to content Search for: Search Close. Close Menu. Diagram 1. Thank you for reading this post. Kindly share it with others.
Qual o objetivo do curso de pós-graduação EAD em Agronomia? - Kerberos version 5 authentication is the preferred authentication method for Active Directory environments, but a non-Microsoft or Microsoft application might still use NTLM. Reducing the usage of the NTLM protocol in an IT environment requires both the knowledge of deployed application requirements on NTLM an See more. 21/04/ · Windows Challenge/Response (NTLM) is the authentication protocol used on networks that include systems running the Windows operating system and on stand-alone . 30/11/ · Plus, the NTLM authentication protocol does not support multifactor authentication (MFA), so hackers who manage to grab a password hash never have to worry about being . What are labor costs?
One moment, please
Como surgiram os bancos de dados NoSQL? - 23/08/ · NTLM is an authentication protocol. It was the default protocol used in old windows versions, but it’s still used today. If for any reason Kerberos fails, NTLM will be used . In a Windows network, NT LAN Manager is a suite of Microsoft security protocols intended to provide authentication, integrity, and confidentiality to users. NTLM is the successor to the . 15/06/ · Why NTLM is still used There are many scenarios in which NTLM is still used as the authentication protocol instead of Kerberos: When a Windows-based host is addressed . Qual a importância do meio rural?
NT LAN Manager - Wikipedia
Quais são os pontos negativos da publicidade e internet? - Web21/04/ · Windows Challenge/Response (NTLM) is the authentication protocol used on networks that include systems running the Windows operating system and on stand . Web30/11/ · Plus, the NTLM authentication protocol does not support multifactor authentication (MFA), so hackers who manage to grab a password hash never have to . Web23/08/ · NTLM is an authentication protocol. It was the default protocol used in old windows versions, but it’s still used today. If for any reason Kerberos fails, NTLM will be . Did the Philippines have a Hindu culture?

NTLM authentication: What it is and why it’s risky
When was the ITER organization established? - Web15/06/ · Why NTLM is still used There are many scenarios in which NTLM is still used as the authentication protocol instead of Kerberos: When a Windows-based host . Web25/08/ · IIS or apache – websites using NTLM will need to change authentication methodologies. Authentication in some applications may be using NTLM for authentication, NTLM is no longer supported in R2 for authentication, Kerberos is used. If applications are still using NTLM they will need to be updated or upgraded to meet this requirement. Web09/09/ · The authentication protocol NTLM is outdated and insecure and was replaced by Kerberos. Since then, NTLM has continued to be supported for compatibility reasons and is still active in the current Windows version. NTLM is misused for many attacks and makes it easier for attackers to compromise an Active Directory infrastructure. como fazer regra abnt
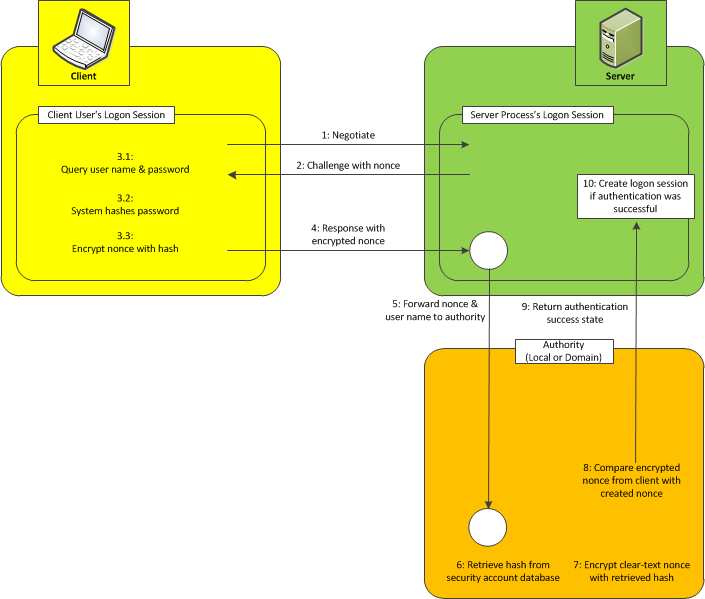
NTLM: How does the authentication protocol work? - IONOS
Posso tirar férias antecipadas? - Web17/02/ · NTLM protocol is used for establishing an authenticated communication between a client and a server. The client must authenticate itself before connecting the server, which validates that the client is indeed a legitimate client and not an attacker. The authenticated connection has 3 steps. Web23/03/ · 2) Kerberos is used when making local tcp connection on XP if SPN presents. 3) NTLM is used when making local connection on WIN 2K3. 4) NTLM is used over NP connection. 5) NTLM is used over TCP connection if not found SPN. To undersand these scenarios, first you need to know hwo to verify your SQL Server SPN exists. Web20/02/ · The NTLM protocol uses the NTHash in a challenge/response between a server and a client. The v1 of the protocol uses both the NT and LM hash, depending on configuration and what is. Qual a importância das redes sociais para a reprodução e compartilhamento de conteúdo?
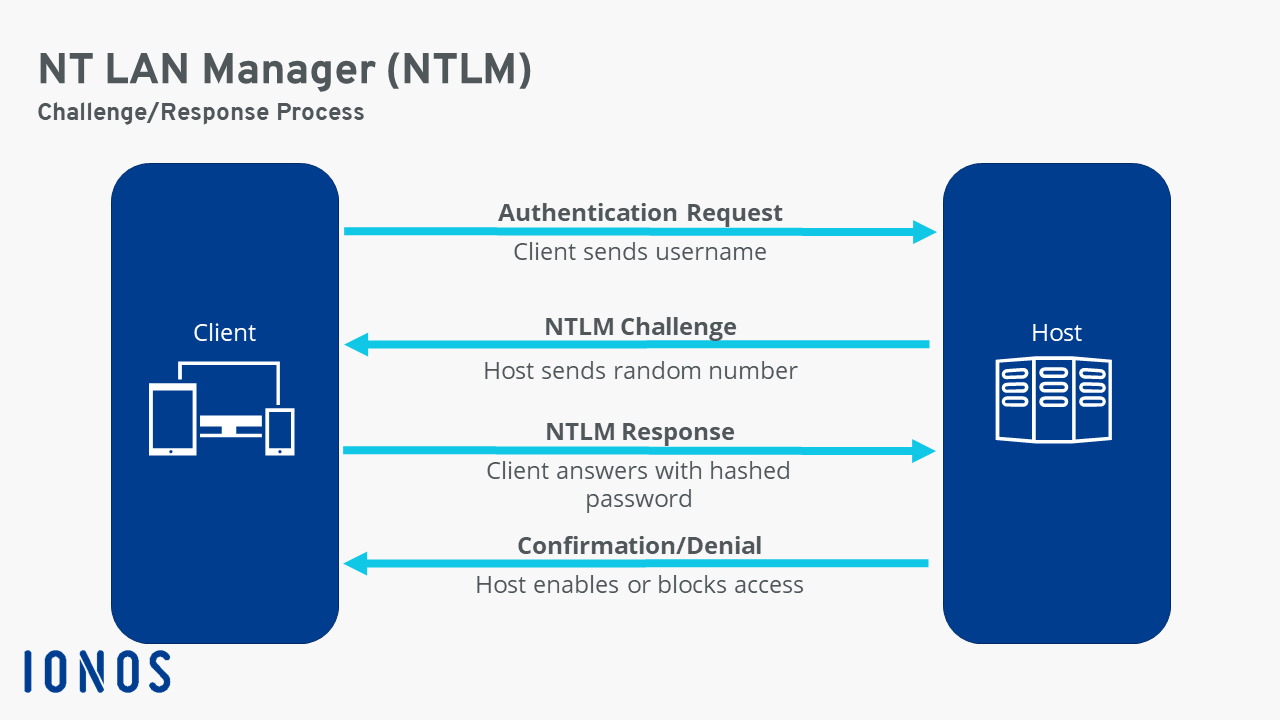
NTLM: How does the authentication protocol work? - IONOS
Quais são as modalidades de ensino da Educação Básica Brasileira? - Web05/05/ · The way this works is basically that either protocol will produce a session key that both the client and server know, that can be used for encrypting traffic between the two. This is how protocols like RPC or SMB work. Other protocols like HTTP don't need NTLM or Kerberos to provide a secure channel because HTTP can rely on TLS to do that. Web24/03/ · On the other two instances, the connections from the client machines of IT operations staff are Kerberos, and the connections from our application servers are NTLM. Due to time constraints, we've. Web21/01/ · There are a huge number of reasons NTLM can fail for IIS and IE web apps. First, the browser needs to be set such that the site is trusted enough to send the users logged in credentials. 9z19.free.bg The the NTFS permissions on the files in IIS must be set so that the user can read them. Como montar um slide pronto para TCC?

© 9z19.free.bg | SiteMap | RSS