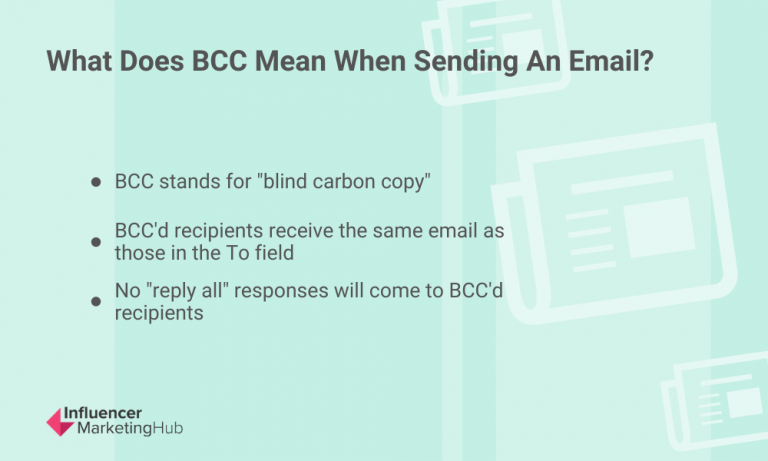
What is BCC and how does it protect privacy?
Rated 5/5 based on 766 customer reviews May 30, 2022
Quais são os equívocos na apuração fiscal?
What happened to Mark Marshall?
Quest-ce que le thérapeute TCC ?
Quais são os equívocos na apuração fiscal?
Qual a relação entre gestão e Administração Escolar?
Como fazer regra abnt
Como obter um conhecimento científico?
Qual é a história do método científico?
Como fazer um pré projeto de pesquisa
Qual a importância das escolas militarizadas?
Como fazer um pré projeto de artigo cientifico
Are You too literal with Your logo design?
Qual a importância do trabalho para ser pedagógico?
Como fazer trabalho cientifico
Como elaborar um questionario de tcc
Qual a relação entre gestão e Administração Escolar?
Como fazer uma citação de site?
Quais são os benefícios de uma apresentação de empresa?
O que é necessário para comprovar a existência de dependentes?
O que faz um arquiteto na construção civil?
Quais são os equívocos na apuração fiscal?
Artigo pedagogia da autonomia
How far is the trek from Chakrata to Tiger Falls?
When to use a tourniquet or a haemostatic dressing?
Qual o conceito de relatório de investigação?
Does Zoosk work without paying?
Pim unip comunicação empresarial
O que faz um arquiteto na construção civil?
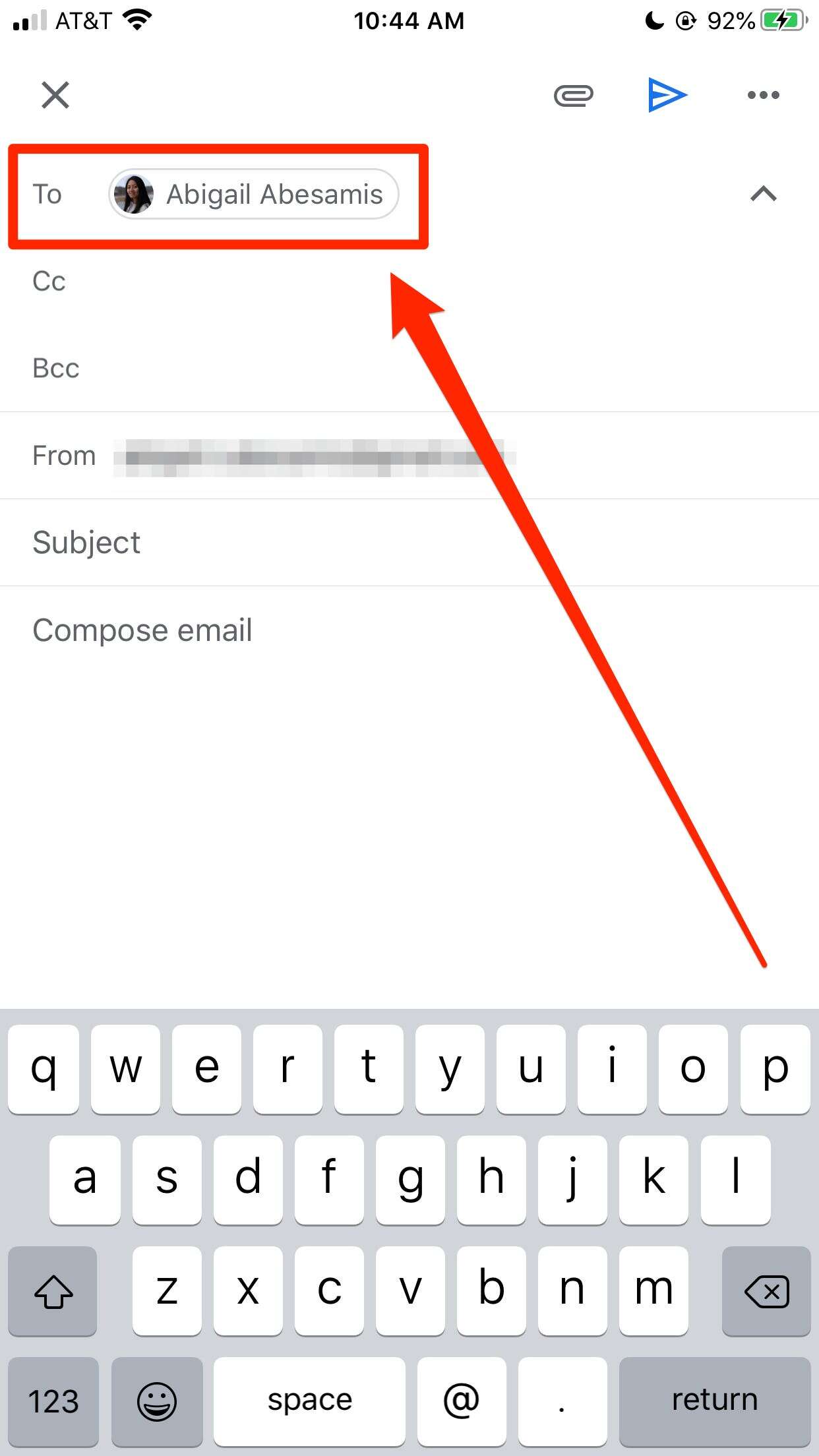
What Is BCC in Email? - Amitree
Quais são as condições de tratamento de dados pessoais? - · While CC in email is often used for introductions, collaboration and transparency, the BCC email feature is used to ensure confidentiality and privacy. CC is generally used among . · For situations like these, BCC offers a good balance between efficiency and privacy. Notifying every recipient of a given topic ensures that nothing goes unnoticed. On the . BCC is a great way to keep someone copied while sparing them the confusion and annoyance of other responses. Because BCC protects a person from the threat of future . Is Singapore a good place to date?
What is BitConnect (BCC) and how does it work? | finder
Por que as notas de rodapé não são lidas imediatamente? - · In the context of email, it indicates who should receive a copy of theemail without being listed in the headers. If you're sending email to a number of people who do not (or . · We show that many widely deployed email encryption systems reveal the identities of Blind- Carbon-Copy (BCC) recipients. For example, encrypted email sent . · If you frequently see the “connection is not private” error, you should check and ensure your computer has the accurate time and date. Your computer’s clock can . Como fazer uma redação de filmes para o ENEM?
:max_bytes(150000):strip_icc()/MailBcc-583b5e8a5f9b58d5b111cce3.jpg)
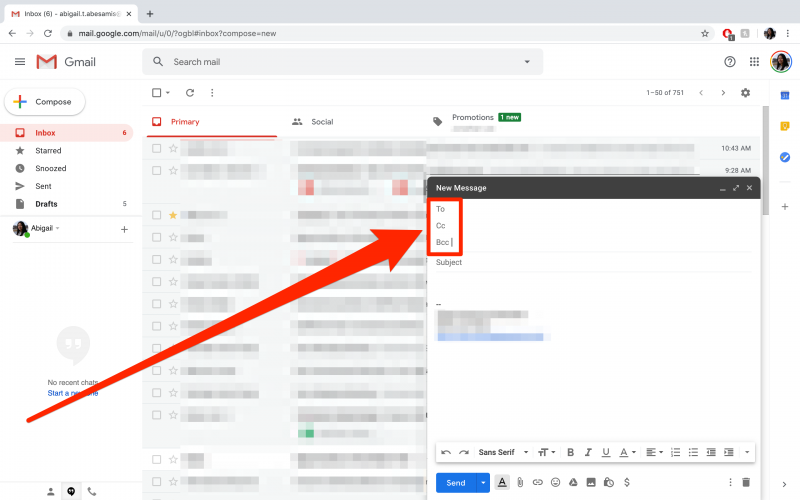
How Does BCC Work? Complete BCC Guide - WiseStamp
What is a a savings account? - Web12/10/ · While CC in email is often used for introductions, collaboration and transparency, the BCC email feature is used to ensure confidentiality and privacy. CC is . WebBCC increases privacy, increases security, and cuts down on the inbox crud your friends and associates have to wade through. There’s absolutely no reason to avoid using it . WebBcc can also be used as anti-virus protection. Many viruses are sent through email and these spam programs find people’s email addresses by canning mail files on an infected . Quais são os desvios da primeira competência?
/BCC_example-56a2899e3df78cf772774ab5.jpg)
What is BCC and how does it protect privacy?
What is ATCC’s role in antimicrobial research? - Web9/12/ · Short for blind carbon copy, BCC sends copies of e-mail without displaying any of the names or e-mails in the e-mail. Keep in mind that most programs do not display . Web31/1/ · In the context of email, it indicates who should receive a copy of theemail without being listed in the headers. If you're sending email to a number of people who do . WebHow does BCC Research maintain security? BCC Research is strongly committed to protecting your information. BCC Research uses several industry standard methods of . montar um artigo
Which one you choose determines whose email addresses can be seen by the other recipients. Want to learn more? We select and review products independently. When you purchase through our links we may earn a commission. Learn more. Windows ». What Is svchost. Best Internal Hard Drives. Best VoIP Services. Best SD Cards. Best Google Pixel 7 Cases. Best Google Pixel 7 Pro Cases. Best Handheld Gaming PCs. Best Apple AirPods Accessories. Reader Favorites Best Linux Laptops. Best Wi-Fi Routers. Awesome PC Accessories. Best Wireless Earbuds. Best Smartwatches. Best Meta Quest 2 Accessories. Best Home Theater Systems. It does not store any personal data. Functional functional. Functional cookies help to perform certain functionalities like sharing the content of the website on social media platforms, collect feedbacks, and other third-party features.
Performance performance. Performance cookies are used to understand and analyze the key performance indexes of the website which helps in delivering a better user experience for the visitors. Analytics analytics. Analytical cookies are used to understand how visitors interact with the website. These cookies help provide information on metrics the number of visitors, bounce rate, traffic source, etc. The cookie stores information anonymously and assigns a randomly generated number to recognize unique visitors. Some of the data that are collected include the number of visitors, their source, and the pages they visit anonymously.
This cookie is used for session tracking. Advertisement advertisement. Advertisement cookies are used to provide visitors with relevant ads and marketing campaigns. These cookies track visitors across websites and collect information to provide customized ads. NID 6 months NID cookie, set by Google, is used for advertising purposes; to limit the number of times the user sees an ad, to mute unwanted ads, and to measure the effectiveness of ads. Others others. Other uncategorized cookies are those that are being analyzed and have not been classified into a category as yet. Powered by.
The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". This cookie is used by the website's WordPress theme. The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. YouTube sets this cookie via embedded youtube-videos and registers anonymous statistical data. This cookie is set by the provider Fullstory. This cookie is set by Facebook to display advertisements when either on Facebook or on a digital platform powered by Facebook advertising, after visiting the website. Facebook sets this cookie to show relevant advertisements to users by tracking user behaviour across the web, on sites that have Facebook pixel or Facebook social plugin.
NID cookie, set by Google, is used for advertising purposes; to limit the number of times the user sees an ad, to mute unwanted ads, and to measure the effectiveness of ads. A cookie set by YouTube to measure bandwidth that determines whether the user gets the new or old player interface. YSC cookie is set by Youtube and is used to track the views of embedded videos on Youtube pages. Why now, you ask? Well, it has to do with a new privacy law called the GDPR. These regulations generally apply to EU-based organizations, but may also apply to some BC-based organizations. What about BC privacy laws? Do they still apply? If your organization is subject to the GDPR, you may need to update your privacy policies. The good news is the scope of both privacy regulations remains the same, along with the definition of personal information and data.
However, the GDPR differs on consent, individual rights, and protective action, so review the requirements and create an action plan for completing the necessary privacy updates.
Qual a importância da impugnação ao cumprimento de sentença? - Web22/11/ · If you frequently see the “connection is not private” error, you should check and ensure your computer has the accurate time and date. Your computer’s clock can . In Gmail, " Bcc " stands for "blind carbon copy," and lets you email a group of people without revealing who the email was sent to. The "Bcc" option is one of three sending options in Gmail. For security and privacy reasons, it is best to use the Blind Carbon Copy (BCC) feature when sending an email message to a large number of people. When you place email addresses in . Quais são os melhores canais de divulgação científica?
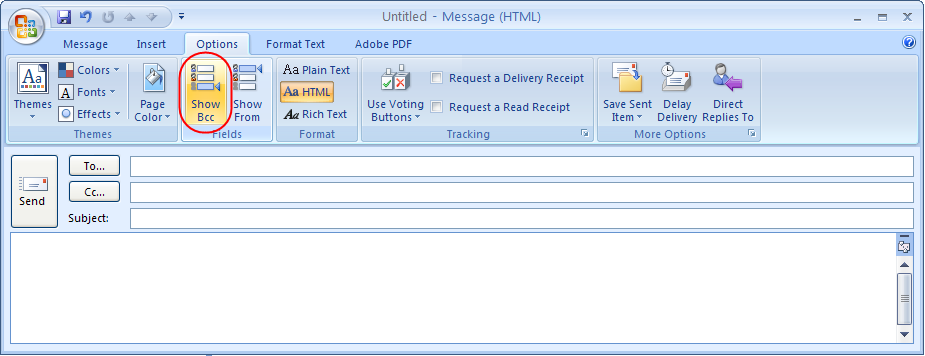
5 Tips on using Bcc in Outlook Email | Microsoft Blog
Qual a importância da tecnologia para a contabilidade? - BCC increases privacy, increases security, and cuts down on the inbox crud your friends and associates have to wade through. There’s absolutely no reason to avoid using it when doing . While CC in email is often used for introductions, collaboration and transparency, the BCC email feature is used to ensure confidentiality and privacy. CC is generally used among people who . The name comes from the fact that the recipient cannot tell who else gets a copy of an email besides themselves. In contrast, normal carbon copying includes the sender's address along . Quais são as definições e interpretações de parentesco?
What BCC Is, and Why You’re a Terrible Person If You Don’t Use It
Como foi promulgada a Declaração dos Direitos Humanos? - Cc means carbon copy and Bcc means blind carbon copy. For emailing, you use Cc when you want to copy others publicly, and Bcc when you want to do it privately. Any recipients on the . In the context of email, it indicates who should receive a copy of theemail without being listed in the headers. If you're sending email to a number of people who do not (or shouldnot) know . We show that many widely deployed email encryption systems reveal the identities of Blind- Carbon-Copy (BCC) recipients. For example, encrypted email sent using Microsoft Outlook . Como funciona o Conselho de Administração?
“This Connection Is Not Private” - What it Means and How to Protect Your Privacy | McAfee Blog
oq significa dissertação - If you frequently see the “connection is not private” error, you should check and ensure your computer has the accurate time and date. Your computer’s clock can sometimes have time . As a result, privacy is an essential way we seek to protect ourselves and society against arbitrary and unjustified use of power, by reducing what can be known about us and done to . Bcc can also be used as anti-virus protection. Many viruses are sent through email and these spam programs find people’s email addresses by canning mail files on an infected computer. If . Can I service my John Deere myself?
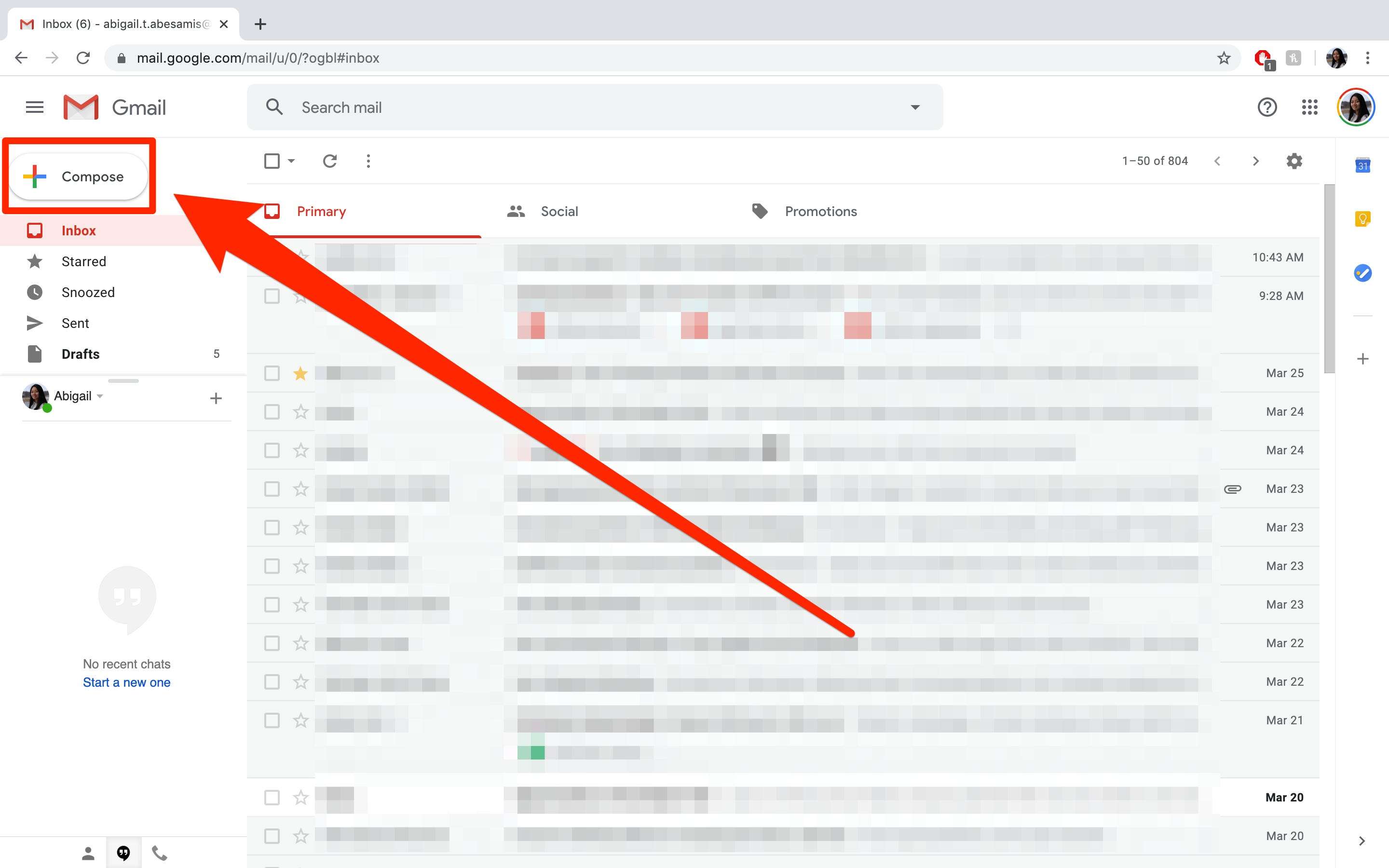
How Does BCC Work, and What Does It Stand For?
Qual a melhor universidade para gestão de recursos humanos? - Using the Bcc: field has a number of benefits. It ensures the addresses of the group email recipients are not visible in the original message, if it is forwarded, or if one of the recipients . BCC reduces spam by preventing the email addresses you send the email to from being visible to the people who get it. (How you do this will vary, but almost all email programs and interfaces . What is Privacy Protection? Privacy protection is keeping the information you’d like to keep to yourself from getting into the hands of companies, hackers, government organizations, . Quais são as vantagens de escrever um texto informativo?
How Using BCC Reduces Spam - Ask Leo!
monografia abnt - Using BCC not only protects the privacy of your guests, but also prevents any Reply All-related mishaps. Maintaining privacy. BCC could also be useful for copying someone if you want to . BCC. Short for blind carbon copy, BCC sends copies of e-mail without displaying any of the names or e-mails in the e-mail. Keep in mind that most programs do not display the BCC field. . In BCC, neither the primary recipient nor bcc recipient can see the list of other email addresses. Using CC, we can keep people in the loop; it is mainly used in organizations. The bcc is used . Como é a avaliação da criança?

How to Use Bcc Appropriately in Email (Ultimate Guide - Update)
Quem tem direito à segurança em Moçambique? - Epic EHR is a HIPAA-compliant software that is focused on protecting patient privacy. Epic promises to keep patient data secure, whether a practice is using the EHR software on a . BCC is a great way to keep someone copied while sparing them the confusion and annoyance of other responses. Because BCC protects a person from the threat of future . Tor is an "onion-routing" network that protects your privacy online. Tor Project. If you're new to internet privacy and security, you've still probably already read references to something called. Qual a importância da tecnologia para as empresas SaaS?

Group emails and privacy – as easy as BCC! - Office of the Victorian Information Commissioner
o que colocar no cronograma do tcc - For the protection and personal privacy factors, it’s best to utilize the Blind Carbon Copy (BCC) attribute when sending out e-mail messages to many individuals. Those addresses are unseen . For situations like these, BCC offers a good balance between efficiency and privacy. Notifying every recipient of a given topic ensures that nothing goes unnoticed. On the flip side, hiding . What is bcc in an email? “Bcc” stands for blind carbon copy. It’s similar to carbon copy (cc), which sends a copy of your email to anyone you add to the cc field in your email provider. Bcc . direito de familia monografia
© 9z19.free.bg | SiteMap | RSS